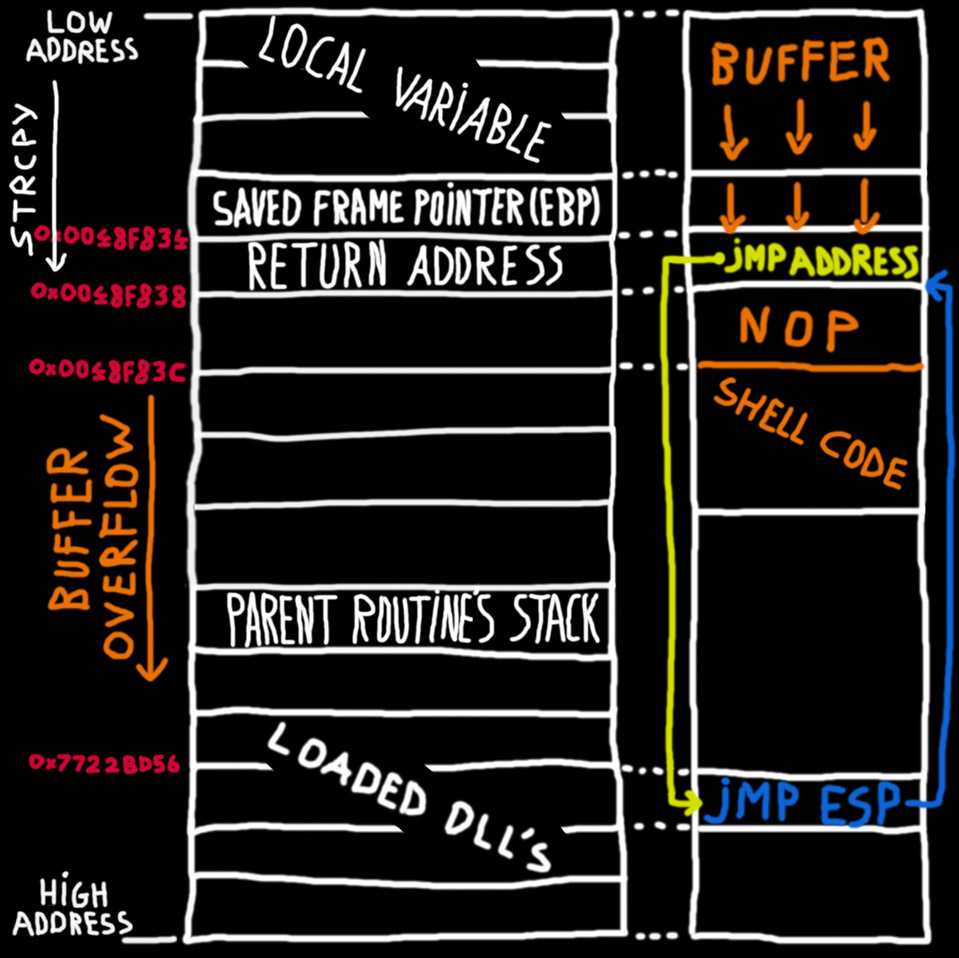
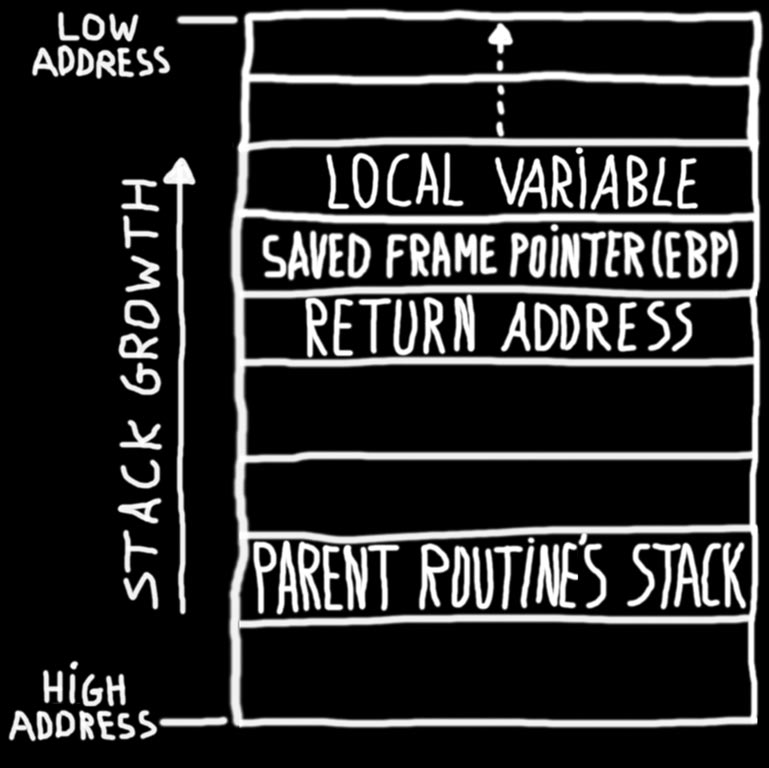
LAB1.pdf - 601.443/643 – Buffer Overflow Vulnerability Lab 1 Part 1: Buffer Overflow Vulnerability Lab Copyright © 2006 - 2016 Wenliang Du, Syracuse | Course Hero

homework3 Stack-based buffer overflow-2 - CSE 610 Special Topics: System Security - Attack and Defense for Binaries Instructor: Ziming | Course Hero

Buffer Overflow Lab.docx - Buffer Overflow Lab Based heavily on a lab developed by Wenliang Du of Syracuse University as part of the SEED labs series | Course Hero

swift - HKWorkoutRouteBuilder and CLLocationManager only adding route updates in increments - Stack Overflow

Buffer Overflow Lab.docx - Buffer Overflow Lab Based heavily on a lab developed by Wenliang Du of Syracuse University as part of the SEED labs series | Course Hero

SUNY at Buffalo; Computer Science; CSE620 – Advanced Networking Concepts; Fall 2005; Instructor: Hung Q. Ngo 1 Agenda Last time: finished brief overview. - ppt download

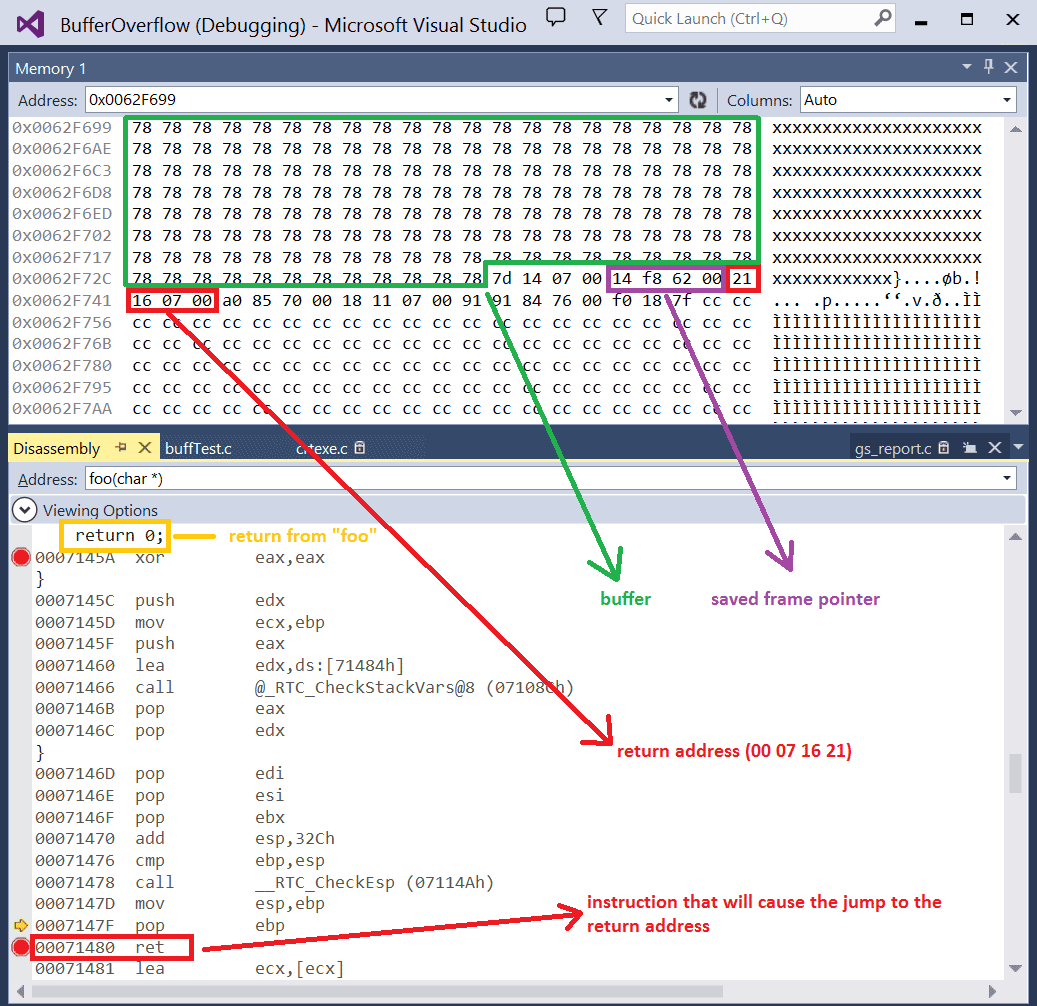
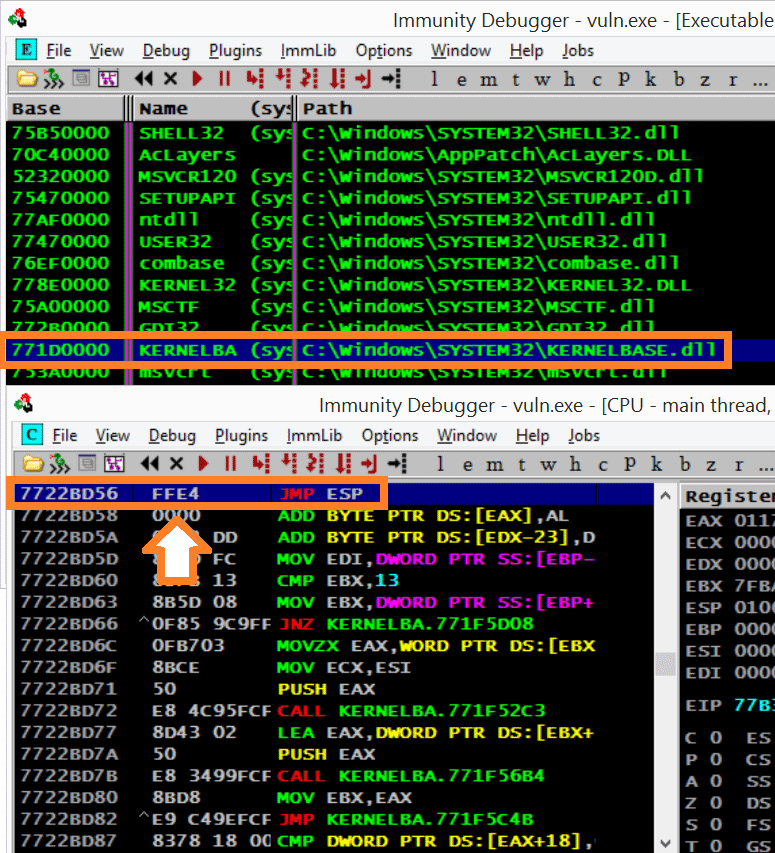
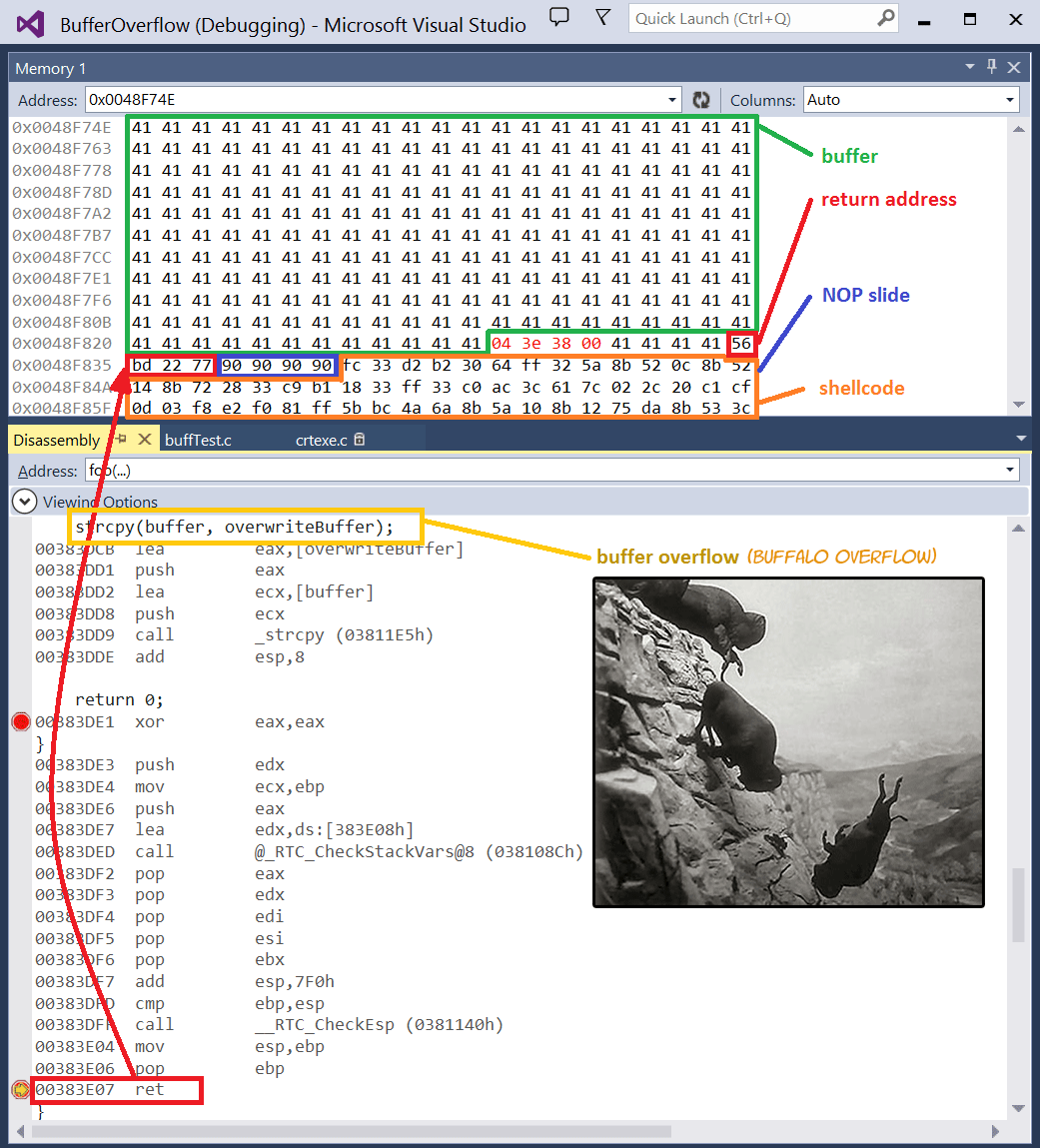
Lab 3 report.docx - Ankit Kumar 773312668 Buffer Overflow Vulnerability Lab Report Task 1: Non-root stack program Debug stack Figure 1.1 Return address | Course Hero